Types of software and interrupts
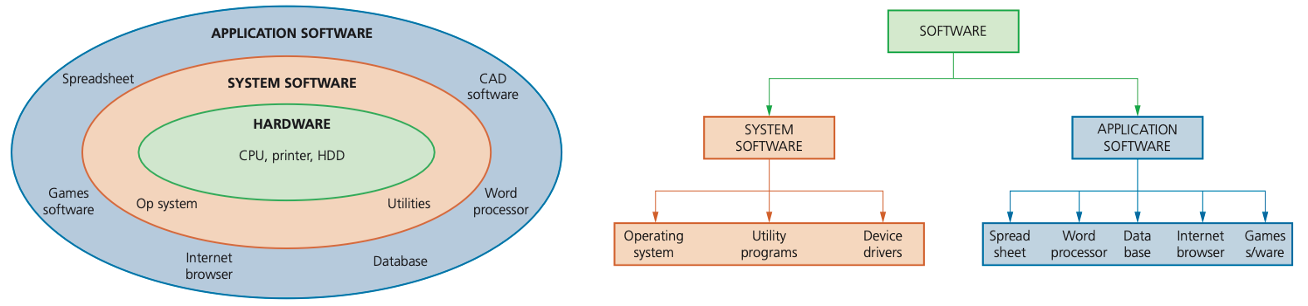
System software and application software
All computers begin life as a group of connected hardware items.
General features of system software
- set of programs to control and manage the operation of computer hardware
- provides a platform on which other software can run
- required to allow hardware and software to run without problems
- provides a human computer interface (HCI)
- controls the allocation and usage of hardware resources.
General features of application software
- used to perform various applications (apps) on a computer
- allows a user to perform specific tasks using the computer’s resources
- may be a single program (for example, NotePad) or a suite of programs
- user can execute the software as and when they require.
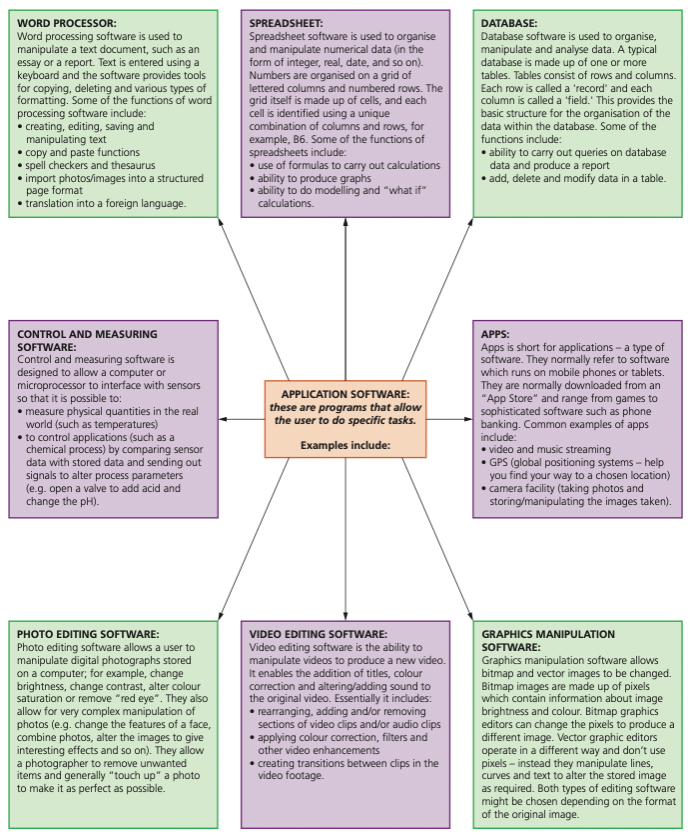
Examples of typical application software
- APPLICATION SOFTWARE: these are programs that allow the user to do specific tasks.
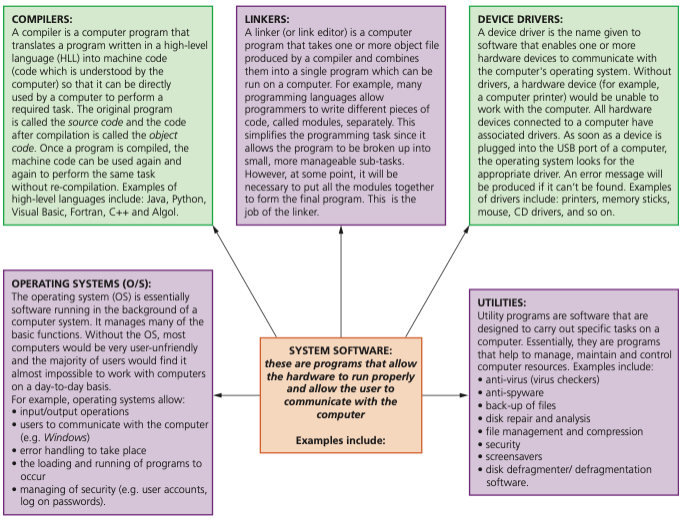
Examples of typical system software
- SYSTEM SOFTWARE: these are programs that allow the hardware to run properly and allow the user to communicate with the computer
Utility software (utilities)
Computer users are provided with a number of utility programs (often simply referred to as utilities) that are part of the system software.
Utility programs are often initiated by the user, but some, notably virus checkers, often just run in the background without the need for any user input.
Utility programs offered by most computer system software include:
- virus checkers
- defragmentation software
- disk contents analysis and repair
- file compression and file management
- back-up software
- security
- screensavers
Virus checkers (anti-virus software)
- Running anti-virus software in the background on a computer will constantly check for virus attacks.
- Although various types of anti-virus software work in different ways they all have the following common features:
- they check software or files before they are run or loaded on a computer
- anti-virus software compares a possible virus against a database of known viruses
- they carry out heuristic checking – this is the checking of software for types of behaviour that could indicate a possible virus; this is useful if software is infected by a virus not yet on the database
- any possible files or programs which are infected are put into quarantine which:
- allows the virus to be automatically deleted, or
- allows the user to make the decision about deletion (it is possible that the user knows that the file or program is not infected by a virus
- this is known as a false positive and is one of the drawbacks of anti virus software)
- anti-virus software needs to be kept up to date since new viruses are constantly being discovered
- full system checks need to be carried out once a week, for example, since some viruses lie dormant and would only be picked up by this full system scan.
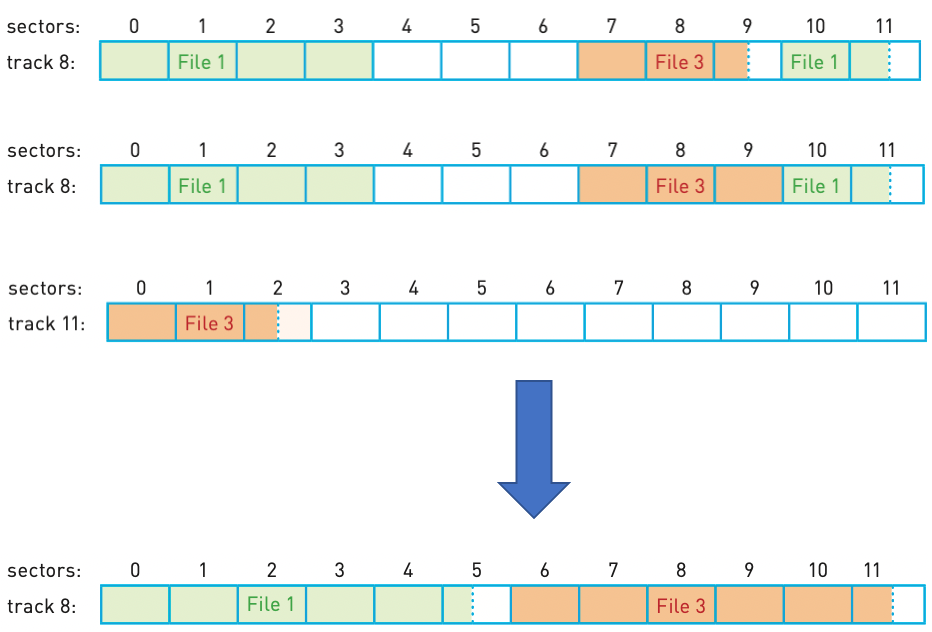
Defragmentation software
- As a HDD becomes full, blocks used for files will become scattered all over the disk surface.
- It would obviously be advantageous if files could be stored in contiguous sectors considerably reducing HDD head movements.
- A disk defragmenter will rearrange the blocks of data to store files in contiguous sectors wherever possible.
Back-up software
While it is sensible to take manual back-ups using, for example, a memory stick or portable HDD, it is also good practice to use the operating system back-up utility. This utility will:
- allow a schedule for backing up files to be made
- only carry out a back-up procedure if there have been any changes made to a file.
Windows uses File History, which takes snapshots of files and stores them on an external HDD at regular intervals.
Mac OS offers the Time Machine back-up utility.
Security software
- Security software is an over-arching utility that:
- manages access control and user accounts (using user IDs and passwords)
- links into other utility software, such as virus checkers and spyware checkers
- protects network interfaces (for example, through the use of firewalls)
- uses encryption and decryption to ensure any intercepted data is meaningless without a decryption key
- oversees the updating of software (does the update request come from a legitimate source, for example).
Device drivers
- Device drivers are software that communicate with the operating system and translate data into a format understood by a hardware peripheral device.
- All USB device drivers contain a collection of information about devices called descriptors; this allows the USB bus to ask a newly connected device what it is. Descriptors include vendor id (VID), product id (PID) and unique serial numbers.
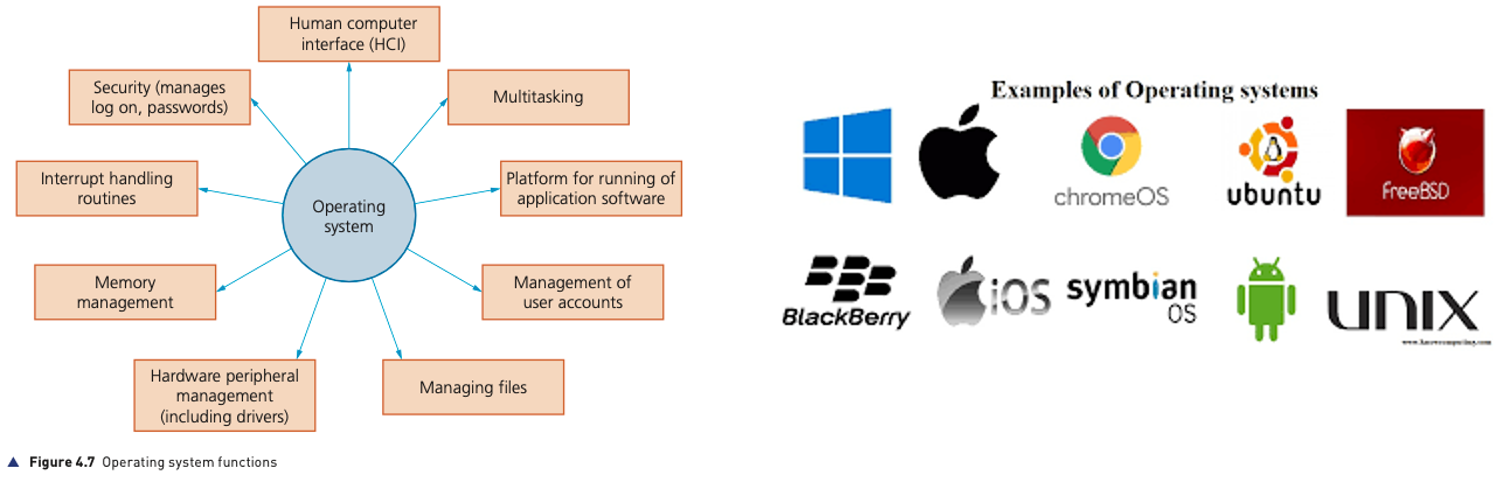
Operating systems
- To enable computer systems to function correctly and allow users to communicate with computer systems, software known as an operating system needs to be installed.
- An operating system provides both the environment in which applications can be run and a useable interface between humans and computer.
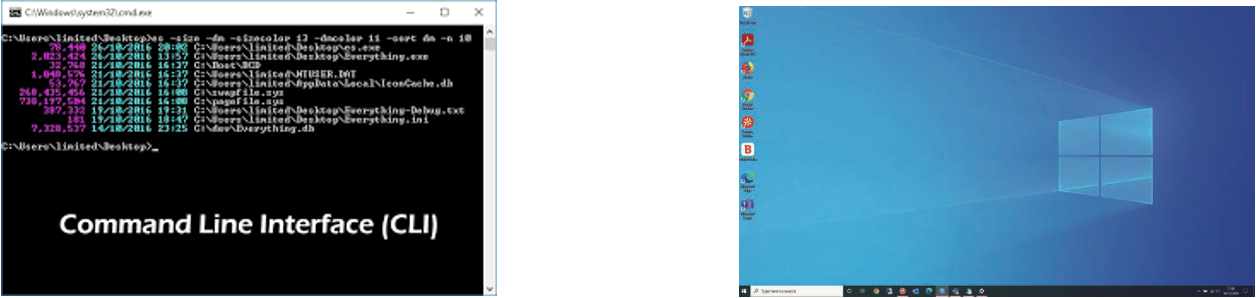
Human computer interface (HCI)
The human computer interface (HCI) is in the form of a Command Line Interface (CLI) or a Graphical User Interface (GUI).
GUIs use various technologies and devices to provide the user interface. One of the most common is WIMP (windows icons menu and pointing device), which was developed for use on personal computers (PC).
CLI vs GUI
| Interface | Advantages | Disadvantages |
|---|---|---|
| command lineinterface (CLI) | the user is in direct communicationwith the computer the user is not restricted to a number of pre-determined options it is possible to alter computer configuration settings uses a small amount of computer memory | the user needs to learn a numberof commands to carry out basicoperations all commands need to be typed inwhich takes time and can be error-prone each command must be typed inusing the correct format, spelling,and so on |
| graphical userinterface (GUI) | the user doesn't need to learn any commands it is more user-friendly; icons areused to represent applications a pointing device (such as a mouseis used to click on an icon to launchthe application - this is simplerthan typing in commands or atouch screen can be used whereapplications are chosen by simply touching the icon on the screen) | this type of interface uses up considerably more computer memory than a CLl interface the user is limited to the icons provided on the screen needs an operating system, such asWindows, to operate, which uses upconsiderable memory |
Memory management
- Memory management carries out the following functions:
- manages the primary storage (RAM) and allows data to be moved between RAM and HDD/SSD during the execution of programs
- keeps track of all the memory locations
- carries out memory protection to ensure that two competing applications
- cannot use the same memory locations at the same time.
Security management
- Security management is another part of a typical operating system; the function of security management is to ensure the integrity, confidentiality and availability of data. This can be achieved as follows:
- ensuring that anti virus software (and other security software) is always up to
- by carrying out operating system updates as and when they become available date, preserving the integrity, security and privacy of data
- by communicating with, for example, a firewall to check all traffic to and from the computer
- by making use of privileges to prevent users entering ‘private areas’ on a
- computer that permits multi-user activity (this is done by setting up user accounts and making use of passwords and user IDs); this helps to ensure the privacy of data
- by maintaining access rights for all users
- by offering the ability for the recovery of data (and system restore) when it has been lost or corrupted
- by helping to prevent illegal intrusion into the computer system (also ensuring the privacy of data).
Hardware peripheral management
- Hardware management involves all input and output peripheral devices. Hardware management:
- communicates with all input and output devices using device drivers
- uses a device driver to take data from a file (defined by the operating system) and translates it into a format that the input/output device can understand
- ensures each hardware resource has a priority so that they can be used and released as required
- manages input/output devices by controlling queues and buffers;
File management
- The main tasks of file management include:
- file naming conventions which can be used i.e. filename.docx (where the extension can be .bat, .htm, .dbf, .txt, .xls, etc.)
- performing specific tasks (for example, create, open, close, delete, rename, copy, and move)
- maintaining the directory structures
- ensuring access control mechanisms are maintained (for example, access rights to files, password protection, or making files available for editing or locking them)
- ensuring memory allocation for a file by reading it from the HDD/SSD and loading it into memory.
Multitasking
- Multitasking allows computers to carry out more than one task (i.e. a process) at a time.
- Each of the processes will share the hardware resources under the control of the operating system software.
- To make sure that multitasking operates correctly (in other words, the processes don’t clash with each other), the operating system needs to constantly monitor the status of each of the processes under its control:
- resources are allocated to a process for a specific time limit
- the process can be interrupted while it is running
- the process is given a priority so it can have resources according to its priority (the risk here is that a low priority process could be starved of resources).
Management of user accounts
- Computers allow more than one user to log onto the system.
- It is therefore important that users’ data is stored in separate parts of the memory for security reasons (also refer to security management earlier in this section).
- Each person logging onto the computer will be given a user account protected by a user name and password.
- The operating system is given the task of managing these different user accounts.
- This allows each user to:
- customise their screen layout and other settings
- use separate folders and files and to manage these themselves.
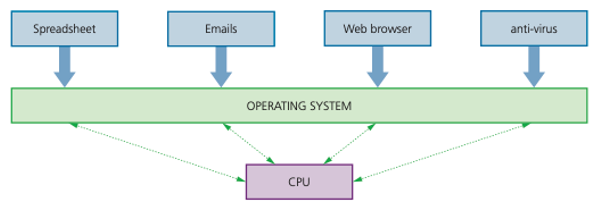
Running of applications
When a computer starts up, part of the operating system needs to be loaded into RAM – this is known as booting up the computer (or a bootstrap loader).
The start-up of the computer’s motherboard is handled by the basic input/output system (BIOS).
The BIOS tells the computer where the storage device that holds the operating system can be found; it then loads the part of the operating system that is needed and executes it.
The BIOS is often referred to as firmware.
Firmware is defined as a program that provides low level control for devices.
The BIOS program is stored in a special type of ROM, called an EEPROM (Electrically Erasable Programmable ROM).
EEPROM is a flash memory chip, which means its contents remain even when the computer is powered down.
However, it also means the BIOS can be rewritten, updated or even deleted by a user.
Once the CMOS is re-started, it will access the same BIOS program from EEPROM, but the settings will now be the default factory settings.
Consequently, if a user has changed the BIOS settings (for example, the clock speed), the settings will revert to those settings made at the factory once power is restored to the CMOS.
The application software will be under the control of the operating system and will need to access system software such as the device drivers while it is running.
Different parts of the operating system may need to be loaded in and out of RAM as the software runs.
Interrupts
An interrupt is a signal sent from a device or from software to the microprocessor. This will cause the microprocessor to temporarily stop what it is doing so that it can service the interrupt. Interrupts can be caused by:
- a timing signal
- an input/output process
- a hardware fault
- user interaction
- software errors
Once the interrupt signal is received, the microprocessor either carries on with what it was doing or stops to service the device or program that caused the interrupt.
The computer needs to identify the interrupt type and also establish the level of interrupt priority.
Interrupts allow computers to carry out many tasks or to have several windows open at the same time.
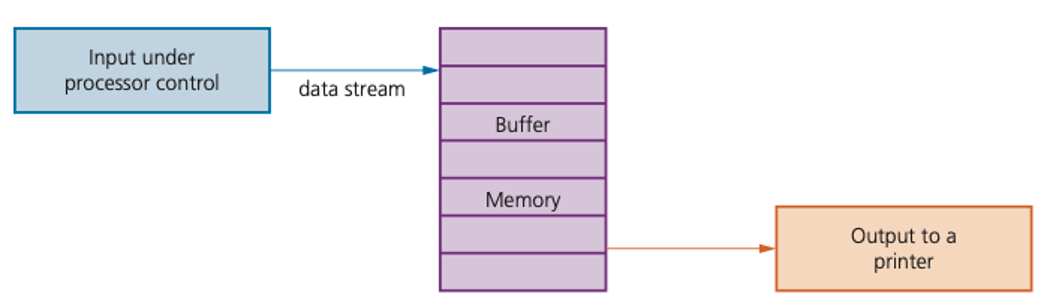
This can all be achieved by using an area in memory known as a buffer.
A buffer is a memory area that stores data temporarily
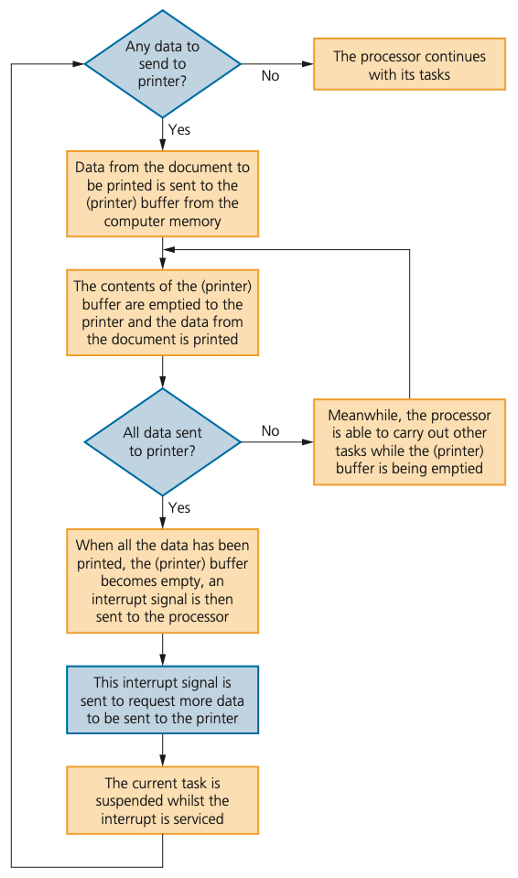
Whenever an interrupt is received it needs to be serviced.
The status of the current task being run first needs to be saved.
The contents of the Program Counter (PC) and other registers are saved.
Then the interrupt service routine (ISR) is executed by loading the start address into the Program Counter (PC).
Once the interrupt has been fully serviced, the status of the interrupted task is reinstated (the contents of all the saved registers are then retrieved) and the process continues.
Buffers and interrupts are often used together to allow standard computer functions to be carried out.